You are what you present!
Identity is a mathematical term belonging to the scientific theory of social mathematics, originally studied in the late 18th century by French mathematician and philosopher, Marie Jean Antoine Nicolas de Caritat, Marquis de Condorcet.

Simply speaking, identity is a combination of traits that define who a particular subject is. However, characteristics identifiable during a personal interaction do not consider the impact of distance and devices in our connected world. This world is where identities are represented by databases belonging to others filled with information that we provide. Such Information stores are then managed by automation and perpetuated thru merger and acquisition. Processes fraught with peril and pitfall, indeed.
We have effectively created numerous “digital twins” that loosely connect with us by biometric and alphanumeric authentication methods based on our unvetted, untested information. This lack of a secure, federated identity solution and broadly applied loose assumptions of trust, opens doors to threats from all directions and levels of sophistication.
Independent platforms developed by governments and commercial institutions cannot offer and test a federated identity, a state of trust is just assumed across the infrastructure of choice. Identifying a person relying on a single, aging data sample or biographical reference is inherently weak. The systems in use today, lack the ability to test the validity of participants for higher-order environmental or technological threats.
DISTINCT ID, A GLOBAL SOLUTION

Identifying a person relying on a single, aging data sample or biographical reference is inherently weak. The systems in use today, lack the ability to test the validity of participants for higher-order environmental or technological threats.
Distinct IDentification (DID) consists of sequences that identify the point of origin (person and/or device), and the instance of the particular transaction. DID sequence codes are encrypted by proprietary data obfuscation handled by trust agents integrated with Eigenstate Transceivers. Once structured according to the DID persona of interest, the formally secured, client-centric information collected and vetted is used to verify the person of origin and point of origin, together with destination details and thus, provenance is proven.
Ensuring You Are You
Verified Identity
Automated verification to establish and maintain trust, verify time of use, and implement protocols that lead to transactional confidence.
Measuring Event Stress
Behavior Analytics
Layered defenses against ever-evolving fraud attempts by monitoring use, time of contact, and other continual environmental condition testing.
Meeting Industry Requirements
Compliance Assurance
Automated key compliance processes and use testing to establish and maintain a user behavior historical profile consistent with standards..
BUILDING A SECURE IDENTITY and DIGITAL TWIN
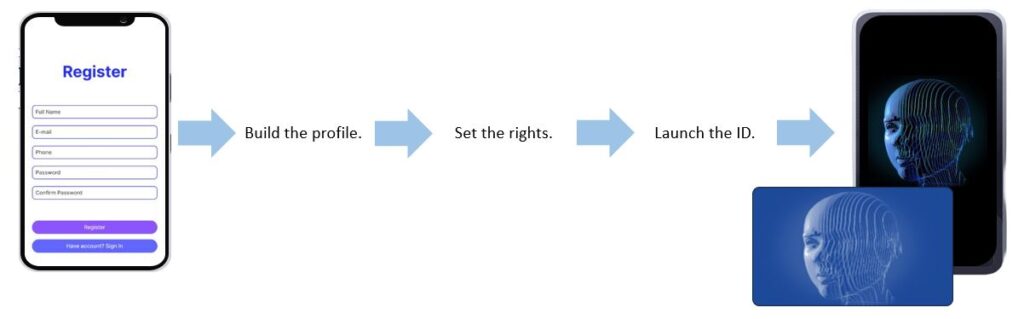
From the completion of an MFA based application process, a user-appropriate level of security is applied, and a circle of trust is established throughout the body of users and peers associated to the new user and confirmed by such party, creating unique trusted community of contacts. Once constructed by the DISTINCT user and their environment, their secured digital twin provides thoughtful access for all commercial and private activities.
DISTINCT ID 4POINT AUTHENTICATION
Credible digital identities must consist of more than a name, address, phone number and password, and protect the user’s from the ability of technology to mimic or steal their identity. DID/4PA creates a unique multipart digital sequence for each registered individual, with each data set requiring translation by a trust agent complete with associated Eigenstate Transceiver. The proprietary combination of VTI techniques and methods remove attack vectors and delivers stronger security against technical and human attack methods.
In addition to a profile of the user’s characteristics, DID uses VSF to provide for the setting of rights and access by third-party applications. This feature helps to ensure that systems requesting identity confirmation become aligned, while opening the door to new unrealized applications.
DISTINCT ID’s may be presented by VSF secured software in a phone app, a smart card or by virtual device. Frictionless adoption by a client application is accomplished through a facility that opens an independent services window, access is through a thin security bar that may be accessed at the top of any screen. The services window also provides access to event policing actions.
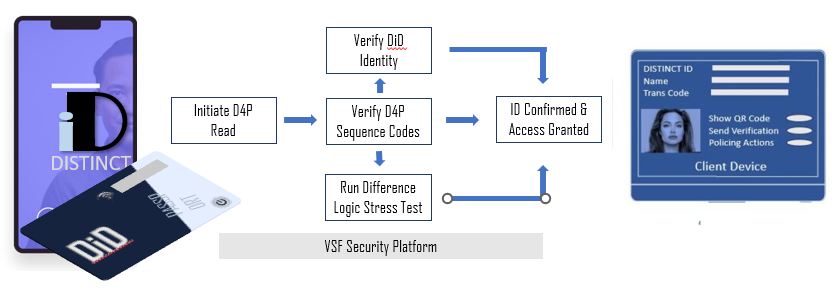
DID plus 4POINT (D4P) may populate the services window with client-centric information that may include a facial picture, an identification and sequence code, or other features that meet requested functionality. D4P applications that are strongly associated to D4P smart cards may operate independently in situations where a network is not present. Additionally, D4P can be customized to suit any authentication requirement.
All user personal data is kept hidden and DID codes are encrypted. EigenTx Trust Agents perform trust calculations based upon personal responses Local VSF data agents handles network-not-available events and provide the relevant encryption/decryption services.
THE D4P SMART ID CARD
In support of the global search for Trust in Identity, uniquely manufactured cards are being adopted for travel, healthcare, banking and other commercial activities. In many cases, a card, NOT a smartphone app is the technology of choice. The enhanced DID platform extends protection to interact with the card itself. DID with 4POINT tests for environmental changes in a device (cloning), and social behavior or undue stress or strain at the time of use (duress or unauthorized user) among other potential inputs.

D4P Identity Cards with onboard intelligence provide visual/physical cues act as Personal Identity and Instance Confirmation (PIIC), compliant with VSF security requirements and providing for initiation of policing options by Trust Agents throughout any interaction, transaction, or transfer.
The DID PIIC allows a single-ended operation to continue for resourceful DID users to grow trust and build messages and files for use in the wild, on LANs, community Wi-Fi, and even Flash Stick “sneaker networks.” The VSF security barrier affords the user control over the public use of their private data. D4P provides a correlation to effectively resolve most transactions with or without the connectivity or the frictional overhead of other identity paradigms fashioned for security.