VSF is designed to operate above and/or below current security investments, in most cases throughout installations across any established network.
Veil Security Framework (VSF)
Even after security is improved by products and product classes are implemented in so many colorful ways, more than 100 million data breaches occur annually. Questions like Who is knocking and What can be seen MUST be reexamined. Today, the sharing of information requires transactions based on a perceived level of trust between to parties. In globally connected systems that thin layer of implied trust is further diminished by distance and network observers.
The vectors of access and knowledge of what is available must receive increased scrutiny in the next generation of connected systems. Identity, access and knowledge must be connected to enforce information obfuscation to provide an impenetrable data structure capable of enhancing trust. VTI has developed innovative technology to provide agents of trust, allowing our security platform to surpass current offerings by building a new VEIL of TRUST across and throughout the fabric of any network.
The National Institute of Standards and Technology-NIST promotes US innovation and competitiveness by advancing measurement science, standards, and technology in ways that enhance economic security and improve our quality of life. NIST provides a cybersecurity framework that is a voluntary guideline intended to help businesses understand and manage risks.
VSF follows the NIST framework in such a way that Trust is established through a combination of VSF Trust Agents and evidentiary intelligence, with Evidence of Trust Fact (EoTF) protocols overcoming weaknesses seen in worn credentials and ceremonial keys. Payload data is not a benign object within VSF, The payload, its network flight path, and access points along its path play a role in the configuration of cryptographic and authentication handling. VSF is a versatile layer of security protecting against multi vector attack patterns used by today’s advanced persistent threats.
Obscure Intelligence
Remove key sharing, obfuscate data on the device and apply quantum level encryption using pseudo-random game theory to each iteration.
Narrow The Access
Introduce tethered user trust identifiers, access behavior tracking and mobile off-device verification methods to ensure provenance.
Tighten The Pipe
Provide secured data protocols for interpretation by network aware trust agents with Eigen State Transceivers and trust-compliant applications.
VSF Architecture
The VSF core consists of a set of Library API’s, Command line executables, and protocols for validation, verification, access, data and identity security, and transport services. Truly modular, each API function is tied to system requirements of the complete environment in which it is destined and configured to protect. Virtual connections between distributed APIs act to secure communications across the room or around the globe. Trust is the first mission parameter connecting all VSF components, no matter if they are embedded, installed, served, or clouded. VSF considers everything as hostile until genuine status is known and confirmed and then must ensure that all attack vectors are cleared. Exclusively, VSF is designed to operate across ALL currently available security stacks.
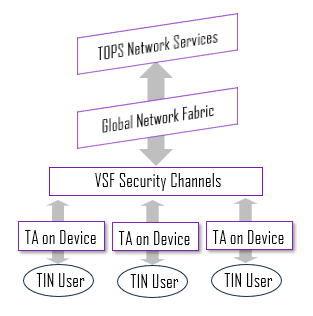
Trust Agent (TA). A small application installed on a device. TA records local data points, establishes the device identifier and anchors itself against any modification. The TA also provides user identification verification services.
Evidence of Trust Fact (EoTF). A data token used to validate a payload, device or user during “Knock and Know” transactions. EoTF creates an evidentiary record used with access credentials and other cryptographic services.
Secure Transaction Operations Protocol (STOP). Initiated by a Trusted Device, STOP is an embedded communication protocol that allows any Trusted Device to become a sender or receiver of properly encoded, secure data.
Trust Oversight Process Service (TOPS). A virtual service providing the “Lens and Link” for trust transactions and administrative services. TOPS servers support network operations guiding payloads through tested flight paths,
Network Edge Connections
Connecting any device or application to the global network means joining an estimated 20 billion devices, today. These devices generate more than 4 zettabytes of data every day. That is a huge target of opportunity.
Within a closed network system or over short-distance communication mediums (Wi-Fi, Bluetooth, etc.), data in flight is often just clear text of your information. Device limitations may not allow encryption, since transaction timing and limited end point processing horsepower hinder the secure abilities from even coming into play.

Phased Binary fast encryption (PBfe) offers a binary handling technique where binary strings are obscured through data science. The data structure is set by end points acting as lightweight Trust Agents, yielding frictionless transactional methods with no loss whatsoever.
VSF combines fast encryption with Trust Identity of user devices and the titled user, securing the edge network from both local and remote bad actor efforts, and establishing a Veil of Trust. VSF also substantiates edge security with a blend of VSF applications for wireless devices including many of the most fashionable mediums.
Internet Safe For Humans
Virtual and augmented reality, distributed data and intelligence, Interactive Multimedia, 5G and 6G networks, IoT, and AI will blur the digital and physical worlds’ boundaries. These technical marvels will arrive at a cost. In this digital age, only an internet that we can TRUST with our images, information, and communications is a suitable foundation for our collective future.
The Next Generation Internet (NGI) is a European Commission initiative that aims to shape the development and evolution of the Internet into an Internet of Trust.

NGI aims to shape the development and evolution of the Internet into an Internet of Humans, which addresses the people’s fundamental needs, including trust, security, and inclusion, while reflecting the values and expected norms all citizens enjoy.
All planning initiatives that involve the future of electronic information must consider data protection, cybersecurity and electronic identity rules necessary to establish a strong trust environment. VTI supports the stated principles of NGI with the distinction that new technologies must apply their principles and power over existing infrastructure, until such time as that infrastructure can be replaced.

True Trust Internet Project (TTIP)
Stringent Core technology tests must pass millions of transactional constructs without error, Veil Technologies is integrating and adapting its VSF platform to create, maintain and operate a trust-based network of devices and applications.
In the first quarter of 2023, we launched a small network of computers employing VSF components to support further developments and to test commercial applications.
TTIP Mission Criteria
Investigate and develop methods to measure and verify devices and their environment at such time as devices are offline, connected at the edge of a network or inside the fabric of a network.
Provide a networking platform to test a distributed and dynamic trust layer operating above existing communication protocols and measures to reduce friction all levels of operation.
Develop an API for applications to operate on a trust layer that secures overall communication, transfer of data and transaction processing and the personal information contained therein.
Test and develop global identity solutions, network communications and platforms consistent with community, commercial and governmental objectives, guidelines, and regulations.
Securing All Intelligence
Connected devices are creating an estimated 328 exabytes of data each day. For our information to maintain integrity and reach our expectations, the data itself must evolve beyond an oblivious state to create and use a much more relevant, guarded and defensible a state of trust throughout.
VSF protects every interaction by establishing a Circle of Trust, independent of other systems and through any network, communication portal, or LAN security system. VSF future-proofing focuses on AI encounters through predefined detection methods and countermeasures.
VSF establishes rules that limit or reduce the value of blind automation and Multiview models. Since VTI knows the inevitable conflict is coming and has abolished potentially automated vectors.

As such, VSF differentiates itself from VPN and other shortsighted security methods. While protecting Point-to-point communication, VSF involves other trusted nodes in verification, vetting, interactive assurances, and transactional details when needed. Further, the superior breadth and depth of VSF serve to maintain Circles of Trust throughout networks while including the protection of individual activities, conversations, transactions, and transfers.
QUANTUM PROTECTION
The movement and storage of information on global networks make any data highly susceptible to broken cryptographic techniques, leaving your critical information open to the possibility of attacks through brute force and insider access credential cloning.
Chaotic Obversion (Cha-Ob) cryptography uses randomized game theory to apply chaotic and obverse methods to hide the data, while embedding unique tokenized data into a Trusted Data Structure called a Cascading Data Haystack. Multi-processor or artificial intelligence driven attacks are rendered ineffective, and key sharing attack vectors are closed since keys and their meaning disappear.
Collections of Haystacks form Headers (HSH), found in logical patterns to determine applied levels of all kinds of security measures. They may also define evidentiary records of the instance of the transaction, and other details of the instance in the moment and with the data in flight or at rest under VSF.











