Technology Development
VTI and our partners continually invest in the development of cybersecurity methods, network systems and applications critical to the delivery of secure trusted digital experiences.

Beyond Root of Trust
The recent history of network breaches and other compromises means that relying on current access and identification methods, key management sharing, authentication and Root of Trust systems that treat the data payload as benign is no longer enough. VTI technology assumes zero-trust and is designed to work with trust tokens, agents and pre-verified devices that produce a greater level of Trust for all users across the fabric of any network.
Eigenstate Transceivers
Similar to a telephonic or physical mail system, the endpoints (nodes) must be identifiable and distinct from other nodes for any type of transaction to occur. In a digital environment that uses virtual not physical locations, the viability of any referenced identity and the constituency of system elements in which the identity reference resides, must be considered to ensure authentication and non-interference.
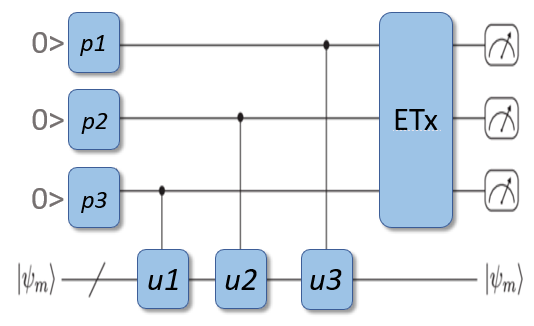
Any node in a connected system can be observed and measured, and a value recorded of that measurement. In quantum mechanics, a measurement of the observable creates an eigenstate, meaning that the value of the observable is exactly known.
Knowledge of a node and its recorded value, offers a method to initiate a reordering of data between a given number of nodes whilst excluding other nodes. VSF encryption and communication applications require node knowledge provided by Eigenstate Transceivers (EigenTx), small agents that can be in software or logically encoded in hardware.
Separate from other network identification methods, the EigenTx introduces a unique user and device identifier that is required for any action to be initiated. The EigenTx harvests system-relevant knowledge and prompts for user or administrator inputs. The Identity is maintained on the local user device, referenced local device data points are continuously tested for verification, and an oversight service records the identity information.
Phased Binary Fast Encryption (PBfe)
Edge networks (Wi-Fi or Bluetooth) used to communicate over shorter distances require a frictionless method to secure data. Phased Binary is a proprietary methodology that reorders binary strings, hiding the intelligence without losing its interpretive meaning. PBfe uses knowledge of the end points as a reference eliminating the need for keys, producing a faster process with less opportunities for cloning or side scanning theft techniques.
PBfe has application inside systems across the copper with iterations preset to the nodes obscuring data up to the entry point of any module. Since the data restructuring method maintains the intelligence within the string, PBfe future systems may include processing abilities while the data while encrypted.

Chaotic Obversion Encryption
Chaotic Obversion (also known as CHA-OB (pronounced “KAY-OB”)) was designed to combat and defend against known decoding activities employed by system threats and bad actors. Beginning with this end in mind, the VTI team developed randomly iterative rotating data encryption technology and a simple framework to employ it properly.
The application of integrated random game theory to strictly chaotic and obversive protocols, makes CHA-OB a dynamic challenge when protecting critical data while moving about networks and systems in the wild. CHA-OB works with any data, adding its obfuscation to any other cases of encryption before, after, or on both sides of a payload.
The resulting content, obfuscated by Cha-Ob includes protocols determined by the chosen level of security, control and protections that are tagged to the content. Both data and content are packaged together forming an obfuscated package matching the original in form with zero loss (strings of text, a file, a stream, or an encrypted item of similar nature).
In application, VSF integrates a novel encryption method requiring node knowledge with an eigenstate transceiver, increasing the node’s secure connection capabilities. Furthermore, VTI’s Veil of Trust establishes a secure framework to securely communicate or archive logic, information, or both.
Chaotic Obversion and Phased Binary are proprietary technologies that work with intranodal values (general and local eigenstates), minutely restructuring data to obscure any and all intelligence without relying on key-sharing methods whatsoever.
Trust Protocol Authentication

Consistent with the focus on trusted systems and transactions, VTI has developed authentication methods that enhance current Multifactor Authentication (MFA). Current systems assume rights, lacking the ability to test the environment or provenance of the individual at the time of use. The VTI authentication algorithm introduces new protocols that can be applied to off-device card platforms and application log-in methods.
- 1. Validity Protocol. Method to validate rights of use at time of a transaction
- 2. Stress Protocol. Method that tests the transaction environment
- 3. Policing Protocol. Method to initiate go/no-go or affect a transaction
Validity
Logic activated at the point of initiation that determines the authenticity of the device and person.
Stress
At the time of a transaction logic tests the initiator for applied pressure from a non-authorized source.
Policing
Dependent on the outcome of Validity and Stress protocols, an action path manages the transaction result.
VTI refers to this technology as MFAPlus which is employed by our proprietary 4Point authentication solution. These protocols work synergistically to provide a trust circle of validity and authentication for use with system access or transactions.
Trust Agent Functions
Transactions are processed through VSF Trust Agents that initiate action, seek to verify the credentials of the user and the intended recipients, and assist with transactional routing tasks. Many action protocols are applied by the Trust Agent, set in motion by the activation of identity verification and an associated transaction. These protocols work synergistically to assure validity and authentication for system access or transactions.
Embedded with VSF Trust Agents are continual tests of environmental behavior and user/device nuances, a feature deployed to prevent device cloning, and ever evolving man-in-the-middle or social attacks. Customizable policing actions are available, examples are simply stopping a transaction or more defensive methods to slow-the-action while other responses are executed. VSF supports multiple levels besides direct connection that may identify the transaction path.
Other criteria of the moment, determined by the type of transaction, distribution of the payload, and the network flight path used for communication serve to strengthen the unique nature of the transaction. Original data (whether previously encrypted or not) is processed through VSF applications to produce oblique payloads, embedding hidden data inspected by Trust Agents along the path.
EoTF and STOP protocols guide network actions continually fortifying the Circle of Trust, completing transactions securely, and recording evidentiary for the transaction in cases of extreme security and/or affirm a legal activity or just maintain confidentiality at a much higher level.
Trust Oversight Process Service
When a Trust Agent is deployed and an identifier is established, data routing and verification features are enabled. A directory function manages a network ear that listens for and initiates Knock and Know queries, regular verification that a node is trusted maintains the connection. Directories are built locally within the TA application and on an oversight service called the Trust Oversight Process Service (or TOPS). This service assists with network connection routing, maintains evidentiary records and provides other security functions.
Trust Oversight Process Services (TOPS) are formed from a group of trust administration services, operating within Secured Servers known to the current network. TOPS Servers connect TA nodes that present properly formatted traffic to reach one another.
TOPS operates independently of other network technology providing the “Lens and Link” for extending trust across all transactions and administrative services faced by the network of choice. TOPS Server Systems share data over the network using proprietary STOP protocol, embedded in the payload to provide verification and routing information.

Network communications based on packet switching techniques and established protocols are unaffected, allowing the gradual implementation of the entire range of VEIL Trust Strategies with distributed oversight across all network mediums. This secondary topology supports adjustments to levels of Quality of Service (QoS) and Priority of Service (PoS).
As TOPS expands, traffic will enjoy better security through direct obfuscation and fade from view on currently active virtual communication circuits. A TOPS Network Operations Center will address any exceptions arising from operations such as loss of connection, inability to authenticate, or any other user concern.
VSF Processors
The adoption of smart sensors, intelligent automobile systems, and the global Internet of Things increases the number of threat vectors. VSF technology can function as an operating system embedded in chips to provide a security framework on the board, on the copper protecting chip transactions, and applications riding on top.
The path to silicon includes dedicated silicon components and integrations with third-party chipset providers. Scheduled for introduction in 2026.
